
Is there a PE addon to make a HDD read only
#1

Posted 29 November 2009 - 04:02 PM
#2

Posted 29 November 2009 - 04:11 PM
NO.Is there a PE addon that prevents any writes to the HDDs, when i boot from PE?
Not Freeware and not for PE specifically but:
http://www.cftt.nist...write_block.htm
http://www.forensics.../Write_Blockers
Freeware USB write blockers do exist, cannot say whether they work or can work in a PE
http://dsionline.biz..._writeblock.htm
http://www.gaijin.at/dlusbwp.php
http://www.m2cfg.com/downloads.htm
jaclaz
#3

Posted 29 November 2009 - 04:33 PM
Would have expected a free software solution for NT as NT and upwards are notorious for writing to everything within grasp, without asking.
#4

Posted 29 November 2009 - 05:55 PM
Wouldn't a write blocker, be like an overlay driver (ewf /fbwf) with a NUL device for the writes?
#5

Posted 29 November 2009 - 06:07 PM
Thinking about it, i do not understand that no free solution for XP+ exists.
Wouldn't a write blocker, be like an overlay driver (ewf /fbwf) with a NUL device for the writes?
Sure
BTW, while you are at it, you could also write an EWF freeware replacement.
These guys must be really, really smart:
http://www.forensics...log/product.php
to be able to sell (most probably at a very, very dear price
Maybe the "forensic guys" are "scared" by articles like this:
http://www.mykeytech...Blocking2-4.pdf
jaclaz
#6

Posted 29 November 2009 - 06:26 PM
I want simply a little something to stop XP littering on all connected drives. For USB a simple change in the registry does it.
jaclaz you know my point of view in this regard, so i bet you can guess, what i will do instead.BTW, while you are at it, you could also write an EWF freeware replacement.
#7

Posted 29 November 2009 - 06:40 PM
Then it sounds even easier, and even less appear the reason why you cannot do it yourself and share the result, since you find it so easy.I want simply a little something to stop XP littering on all connected drives. For USB a simple change in the registry does it.
The request for a freeware EWF still stands, however.
jaclaz
#8

Posted 29 November 2009 - 07:39 PM
So it hardly is usable unless you always use the same host
medevil - if you use 2k3 sources you can tell the PE not to mount any local disks at boot - maybe that helps
#9

Posted 29 November 2009 - 07:58 PM
#10

Posted 14 September 2010 - 11:01 PM
C:\WinFE\mount\Windows\System32\config\SYSTEM
HKLM\ControlSet001\Services\MountMgr /v NoAutoMount /t REG_DWORD /d 1 /f
HKLM\ControlSet001\Services\partmgr\Parameters /v SanPolicy /t REG_DWORD /d 3 /f
The drives can be toggled online/offline and readonly/readwrite through DiskPart in a command shell.
Also, removing the bootfix file to prevent the option to boot to CD helps make the disc more forensic friendly. Before I try to learn how to script with WinBuilder (I'm new to WinBuilder), can someone tell me an easy way to modify the registry with these two changes and rto emove the bootfix file during the build?
There is a website, www.winfe.wordpress.com that focuses on the forensic version of a bootable PE, but in a more manual effort (and fewer bells and whistles as compared to WinBuilder).
Brett
bshavers@gmail.com
#11

Posted 15 September 2010 - 05:33 PM
Though completely UNLIKE readable, the Winbuilder .script are very similar to good ol' batches, and Winbuilder itself, in a previous incarnation, was called "batcher".
You should have no problems in creating a small .script to add those two Registry keys (or add them to an existing .script).
You can get the Winbuilder help:
http://www.paraglide...Links/links.htm
http://www.paraglide...lp/default.html
and also as a file:
http://www.paraglide.../winbuilder.chm
You want to use the regadd command:
http://www.paraglide...pi/Reg_Add.html
or the Reg_import thingy (easier):
http://www.paraglide...Reg_Import.html
or directly using the Reg2WBSprg.exe:
http://www.boot-land...?...=5049&st=21
About bootfix.bin, you have two choices:
- find which "standard" Winbuilder .script uses/needs it and remove the reference from it
- create a "post processing" .script that removes it afterwards
The command you want to use is probably FileDelete:
http://www.paraglide...html#FileDelete
What is missing from your post is the mention of WHICH actual Winbuilder project are you using as "base", I presume LiveXP, but it could be several other ones.
A "post-processing" .script containing both the registry fixes and the deletion of bootfix.bin is more advisable as it could be compatible to several different projects.
Wonko
#12

Posted 17 September 2010 - 02:01 AM
#13

Posted 17 September 2010 - 02:27 AM
I am also very interested in PE used for forensic investigations.
If you are interested in a tool that creates a 2k3 based PE and asks this during creation
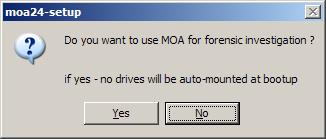
have a look here : http://sanbarrow.com...opic.php?t=1544
In case you are a forensic investigator I would also like to know if this approach to use a PE and mount disks readonly by taking a snapshot first can be used in any way.
Here is a video that shows what I mean
http://sanbarrow.com...s-if-stunt.html
Ulli
#14

Posted 17 September 2010 - 02:42 AM
I'm giving a presentation at SecureWorldExpo next month in Seattle on WinFE/Windows FE and this would be a neat snippet to show as a possibility to work with.
#15

Posted 17 September 2010 - 07:42 AM
I'm giving a presentation at SecureWorldExpo next month in Seattle on WinFE/Windows FE and this would be a neat snippet to show as a possibility to work with.
A word of advice, if I may.
Double check you have actually a forensic MOA for the presentation AND NOT the Wowbagger PE!
http://www.boot-land...?showtopic=8062
We have already seen Windows related presentations become embarassing for the actual speaker.....
Wonko
#16

Posted 17 September 2010 - 09:37 AM
Also, could VirtualBox be used instead of VMware? Vmware is a resource hog whereas Virtualbox seems to run at better speeds ...
Yes - you can use both.
I prefer VMware and from PE I think it is faster then VirtualBOX - at least that is my experience after having used both extensively.
Actually with VMware you have better control about the resources used - that is important in LivCD usage as you probably have no pagefile available.
We have already seen Windows related presentations become embarassing for the actual speaker.....
LOL - thats a good way to get booooed off stage - presenting the Wowbagger PE when the audience expects a forensic one
#17

Posted 17 September 2010 - 03:54 PM
#18

Posted 25 August 2011 - 12:04 PM
WRITEPROT
http://www.joeware.n...eprot/index.htm
http://www.joeware.n...eprot/usage.htm
does and see if it can be replicated/works in a PE.
Wonko
#19

Posted 25 August 2011 - 07:57 PM
edit:
Program is not as good as i first thought or better than i thought depending on your definition.
The program does not stop Windows/PE from writing to the volume. It does something to the volume, that keeps Windows /PE from writing to it.
Just write protected the systemdrive C: from PE. Now i can't boot the installed Windows anymore. Need first to undo the write protect.
So i go out on a limb and say, not suitable for forensics.
#20

Posted 25 August 2011 - 08:21 PM
Appearantly windows can write to the volume at first, but then later decides not to anymore.
The Windows on C: could not boot up anymore and WriteProt showed the drive still write protected, yet somehow the installed windows remembered, that the last boot attempts failed and offered me safe boot options upon start.
#21

Posted 26 August 2011 - 10:11 AM
This may be of help:
http://www.mail-arch...g/msg19282.html
to understand HOW it works WHAT it does.
It must be be some IOCTL in ntdddisk.h
http://www.ioctls.net/
Wonko
0 user(s) are reading this topic
0 members, 0 guests, 0 anonymous users













